A numbers game: Number matching MFA is changing authentication as we know it
Number matching MFA is the next step in protecting your valuable data and Microsoft will soon be implementing it as a default setting on its mobile app.
You might think traditional multi-factor authentication (MFA) is enough to protect your company’s data. Microsoft would disagree. From 8 May 2023, Microsoft will be making number matching MFA the default setting on its mobile app, aiming to stay one step ahead of cyber criminals. Let’s find out more about this change and what it means for authentication and security.
Why? MFA fatigue is real
Although MFA has made it more difficult for bad cyber actors to infiltrate companies, security breaches are still rife. MFA requires the user to authenticate an account sign-in via a mobile application, for example, which sends a push notification to their smartphone. But MFA can be a frustration for users if they are required to frequently authenticate sign-ins. This can lead to MFA fatigue, often resulting in careless behaviour or accidental approval of sign-in requests.
A high-profile example of MFA fatigue resulting in significant amounts of data being stolen was the Uber breach in September last year. A threat actor had used brute force to gain access to the user names and passwords of some Uber employees, and had subsequently bombarded them with repeated push notifications on their mobile devices, urging them to approve the sign-in on their account. All it took was for one annoyed employee to click ‘yes’ on the sign-in prompt. The extent of the data breach is still being assessed, but it may be significant, given that the hacker gained access to Uber’s privileged access management (PAM) solution.
What makes number matching MFA more effective?
Number matching MFA, also known as one-time passcode (OTP) MFA, has been developed to combat MFA fatigue and is generally considered to be more secure than traditional MFA methods. This is because it provides an additional layer of security by requiring the user to provide a unique code that is generated by a device or application. This code is typically only valid for a single use and expires after a brief period of time, making it much more difficult for an attacker to use a stolen password or other credentials to gain access to an account. Additionally, OTPs are not static and can’t be intercepted or stolen like a physical token, biometric or even a SMS message.
MFA fatigue is mitigated as users are required to physically type in the number sent to them, prompting them to think twice about accepting a login. Push notification spam is also not as effective, as users need to know the number and need to have access to the Authenticator app of the account logging on.
Which applications use number matching?
A number of MFA vendors support number matching, including Microsoft, Duo, and Okta. Microsoft has MFA in place for products like Azure Active Directory and Microsoft Authenticator.
From 8 May 2023, Microsoft will be making number matching MFA the default setting for their mobile app, keeping more Microsoft users safer from social engineering attacks.
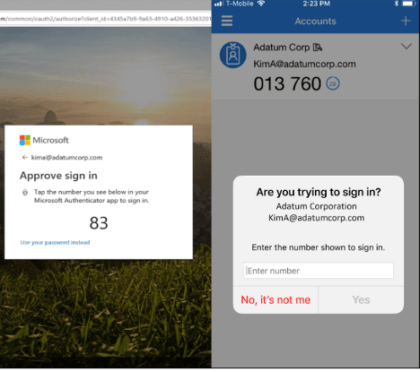
But you don’t need to wait for early May , as number-matching MFA is already set up as an option for accounts. The sooner your company can implement number matching MFA, the sooner you can improve your organisation’s security. But it’s important to have a proper communications plan in place beforehand to get employee buy-in and to ensure they know how this additional security measure will affect their access to certain programmes, systems, and apps. It’s interesting to note, for example, that users will no longer be able to approve sign-in requests from their Apple Watch if their company is using number matching MFA.
Best practices to bear in mind
The Cybersecurity and Infrastructure Security Agency (CISA) in the United States recommends that users should be trained to report unknown or bulk MFA confirmation requests as a precautionary measure. Organisations should also provide regular cybersecurity training on topics such as MFA fatigue, recognising MFA spam, and how to report unknown confirmation requests. In addition, when a user denies a push notification request, the organisation should investigate the cause and alert their IT security team, as it could indicate a compromised password.
Want to know more?
If you’d like to know more about number matching MFA and how to implement it in your organisation, then please get in touch.

Question?
Our specialists have the answer
