The Essential Guide to Cloud Security: Protecting Your Data in the Cloud
The public cloud offers a multitude of advantages for businesses of all sizes. From scalability and cost-effectiveness to increased collaboration and innovation, it’s no wonder so many organisations are migrating their data and applications to the cloud. However, with this shift to the cloud comes a new set of security challenges.
Ekco understands that protecting your data in the public cloud is a top priority. This essential guide will equip you with the knowledge to secure your cloud environment and ensure your data remains safe. Whether you’re a seasoned techie or a curious newcomer, we’ll break down the complexities into clear, actionable steps.
Understanding the Cloud Security Landscape
The cloud security landscape is constantly evolving, with new threats emerging all the time. Here’s a look at some of the most common cloud security challenges:
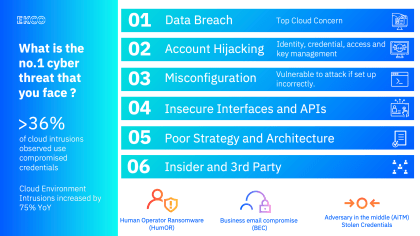
- Misconfiguration: Cloud environments are complex, and even a small misconfiguration can leave your data vulnerable. For example, accidentally leaving a public storage bucket open can expose your sensitive data to anyone on the internet.
- Data Breaches: Cloud data breaches are unfortunately common. Hackers can gain access to your cloud storage through various means, such as phishing attacks or exploiting vulnerabilities in your cloud applications.
- Account Hijacking: If a hacker steals your cloud login credentials, they can access your data and applications, potentially causing significant damage.
- Insider Threats: Insider threats pose a serious risk to cloud security. Malicious insiders can steal data, sabotage systems, or even hold your data for ransom.
- Denial-of-Service (DoS) Attacks: DoS attacks can overwhelm your cloud resources and make your applications unavailable to legitimate users.
The Shared Responsibility Model
When you move your data to the cloud, you enter into a shared responsibility model with your cloud service provider (CSP). This means that both you and the CSP are responsible for securing your data.
- The Cloud Service Provider’s Responsibility: The CSP is responsible for the security of the underlying cloud infrastructure. This includes things like physical security, network security, and virtualisation security.
- Your Responsibility: You are responsible for securing your data and applications in the cloud. This includes things like access control, encryption, and data security.
Building a Secure Cloud Environment
Now that you understand the cloud security landscape and the shared responsibility model, let’s explore the tools and strategies you can use to build a robust cloud security posture.
- Embrace a Layered Approach: Think of cloud security as a layered cake. The foundation is a strong cloud security strategy that aligns with your overall business goals. On top of that, you need a combination of preventative, detective, and responsive measures.
- Preventative Measures:
-
- Access control: Implement strong authentication protocols like multi-factor authentication (MFA) to restrict access to authorised users.
- Data encryption: Encrypt your data both at rest (stored) and in transit (being transferred) to render it useless even if intercepted.
- Regular patching: Keep your software and systems up-to-date with the latest security patches to address vulnerabilities.
-
- Detective Measures:
-
- Security Information and Event Management (SIEM): A SIEM is a powerful tool that collects and analyses log data from various sources in your cloud environment. It can help identify suspicious activity and potential security incidents.
- Security Event Data Recorder (XDR): An XDR solution goes beyond SIEM by not only collecting data from your cloud environment but also from endpoints (laptops, desktops, mobile devices) to provide a more comprehensive view of your security posture.
-
- Responsive Measures:
-
- Security Operations Centre (SOC): A SOC is a team of security professionals who monitor your cloud environment for threats, analyse security data, and take action to contain and remediate incidents.
- Managed Detection and Response (MDR): If you don’t have the resources to staff a dedicated SOC, MDR services can provide the expertise and manpower to detect and respond to security threats around the clock.
-
Ekco Recommends: Don’t be overwhelmed by the alphabet soup of security acronyms (SIEM, XDR, SOC, MDR). Start by conducting a thorough risk assessment to identify your specific vulnerabilities. Then, based on your findings, implement a layered security strategy that incorporates the tools and techniques mentioned above.
Beyond the Tech: Building a Culture of Security
Technology is a powerful tool, but it’s only as effective as the people who use it. Here are some additional tips to cultivate a security-conscious culture within your organisation:
- Security awareness training: Educate your employees about common security threats and best practices to keep your data safe.
- Phishing simulations: Regularly test your employees’ ability to identify phishing
Get the expertise you need and the support you deserve
Cloud security is a complex but essential aspect of running a business in today’s digital age. By understanding the threats, implementing the right tools and strategies, and fostering a culture of security awareness, you can protect your valuable data and ensure the continued success of your organisation.
At Ekco, our specialists can assist you with all of your security requirements, whether it’s finding weak spots, fortifying your defences, educating your employees, or responding to a cyber attack. Schedule a call with our specialists to secure your cloud environment today.

Question?
Our specialists have the answer
