The 7 steps of the cyber kill chain
By Declan Timmons, Director of Cybersecurity Consultancy.
In the event of a cyber attack, cybercriminals go through seven steps
When planning and perpetrating an attack, cybercriminals go through seven steps, which can be divided into three broad categories: preparation, intrusion, and execution. Developed by Lockheed Martin, the Cyber Kill Chain® identifies what adversaries do to achieve their goals.

Preparation
Step 1: Recon
Attackers begin by collecting information. They have various tools at their disposal to do this. Some are very simple, like using LinkedIn to see who works in a company and how the organisational structure works. They can also look at employees’ social media profiles which can often be very revealing. On a technical level, they’ll investigate a company’s infrastructure, where it is relatively easy to find out which systems and software are in use.
In cases where a company is not specifically targeted but part of a broader attack, the primary focus is on known vulnerabilities and identifying organisations that are potentially susceptible to them. One way this can be done by scanning lists of email addresses; If your company is on there, you could potentially become a target of phishing attacks. Attackers target low-hanging fruit, making it critical to have better protection measures in place than your peers.
Step 2: Weaponisation
Next, attackers look at how they gain access to your systems. This can be done through software vulnerabilities, phishing attacks, or other techniques to introduce malicious. The preferred methods are those that don’t require employee interaction, such as exploiting a server that hasn’t been updated.
Intrusion
Step 3: Delivery
As soon as the attackers have picked their targets know what weapons are needed, they proceed to penetrate. This can be done via a phishing email, but in some cases attackers use an exploit. By attacking through a vulnerability, they don’t need an employee to install the malware, making their chance of success higher.
Step 4: Exploitation
Attackers exploit the vulnerabilities they have previously identified to penetrate deeper inside their target’s network and begin taking advantage of this access. They may perform network scans or attempt to intercept passwords.
Step 5: Installation
Once they’re in, they want to make sure they stay in. Attackers aim to embed themselves so that it becomes difficult to remove them. If only one PC gets infected and is discovered and then recovered, the attackers lose their entry point. Therefore, they aim to gain permanent access by installing malicious software on multiple systems.
This allows them to resume the attack at any time. The goal is to infuse as many systems as possible with malware and create backdoor access, so that even after being discovered once, they can continue their attack through another system.
Execution
Step 6: Command and Control
Now is when the damage gets done. Cybercriminals set up a command and control infrastructure. This allows them to manage and control the compromised systems, send instructions to malware, and exfiltrate data. This is crucial for attackers to maintain control over the compromised environment.
Step 7: Actions on Objectives
In this final phase, cybercriminals achieve their specific objectives. This can range from stealing sensitive information to disrupting business operations, demanding a ransom, or other malicious activities that match their intentions.
It is at this stage, that users may notice that things have gone wrong. The might suddenly see a notification appear on their screen that files are encrypted or unavailable. The attackers often make themselves known openly at this stage.
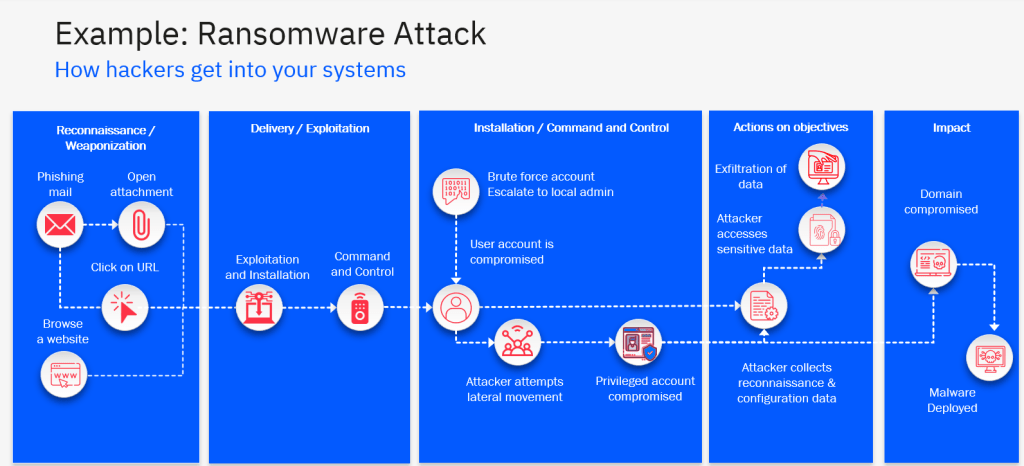
Below is an example of the above steps seen as part of a Phishing and Ransomware attack
If you’d like to discuss how your company can protect itself against cyber attacks then get in touch.

Question?
Our specialists have the answer
