NIST CSF 2.0: Why update it? What’s New? And Why is it important?
By Declan Timmons, Director of Cybersecurity Consultancy.
NIST, the National Institute of Standards and Technology (part of the US Department of Commerce), has updated its Cybersecurity Framework (CSF), with version 2.0. This is a widely recognised set of guidelines, standards, and best practices for managing cybersecurity risks.
Released on 26th February, 2024 following a considerable period of community feedback, this release marks the most significant update to the framework since its initial release in 2014.
Why update it?
CSF 2.0 addresses several key factors and evolving needs within the cybersecurity landscape including:
Emerging Threat Landscape: The cybersecurity landscape is constantly evolving, with new threats, attack vectors, and vulnerabilities emerging regularly. CSF 2.0 incorporates insights from recent cybersecurity incidents and threat intelligence to ensure that organisations have the necessary guidance to address emerging threats effectively.
Feedback and Stakeholder Input: CSF 2.0 reflects feedback and input from a wide range of stakeholders, including government agencies, industry partners, cybersecurity experts, and academia. This input helped identify areas for improvement and refine the framework to better meet the needs of organisations across various sectors.
Advancements in Technology: Technology is continually advancing, introducing new capabilities and challenges for cybersecurity. CSF 2.0 incorporates advancements in areas such as cloud computing, Internet of Things (IoT), artificial intelligence (AI), and machine learning (ML) to help organisations address cybersecurity risks associated with these technologies effectively.
All roads lead to NIST CSF 2.0? (Credit: N. Hanacek/NIST)
What has changed?
Framework Integration: Greater emphasis on integration with other frameworks, standards, and best practices. This integration enables organisations to leverage existing cybersecurity investments and adopt a more holistic approach to managing cybersecurity risks.
Supply Chain Risk Management: Greater emphasis on supply chain risk management, recognising the interconnected nature of modern supply chains and the potential for cyber threats to propagate through them. The framework provides guidance on assessing and mitigating supply chain risks.
Access Control and Identity Management: Expanded guidance on access control and identity management, reflecting the importance of managing user access privileges and authenticating user identities to prevent unauthorised access to systems and data.
Threat Hunting and Detection: Enhanced guidance on threat hunting and detection capabilities, emphasising the importance of proactive threat detection and response strategies to identify and mitigate cybersecurity threats in a timely manner.
Privacy and Data Protection: An increased emphasis on privacy and data protection considerations, aligning the framework more closely with privacy regulations and standards such as the EU General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA).
Measuring and Improving Cybersecurity Maturity: Improved guidance on measuring and improving cybersecurity maturity, helping organisations assess their current cybersecurity posture and develop a roadmap for continuous improvement.
Resource Tiering: Introduces the concept of resource tiering, which helps organisations prioritise and allocate cybersecurity resources based on the criticality of their systems and data assets.
Why is this important?
There are a few interesting points about CSF 2.0 and why it’s important. The first one, is the addition of a new governance feature.
This is the most obvious change in the CSF 2.0. This reflects a growing focus within the cybersecurity community on a top-down approach to risk management. Effectively this assigns more responsibility on senior management to take ownership of the cybersecurity risk management process.
This top-down approach is also evident in the control requirements of the recently released DORA and NIS2 regulations. This is a welcome addition to the framework which provides focus on the importance of senior management involvement in all elements of managing cybersecurity risk.
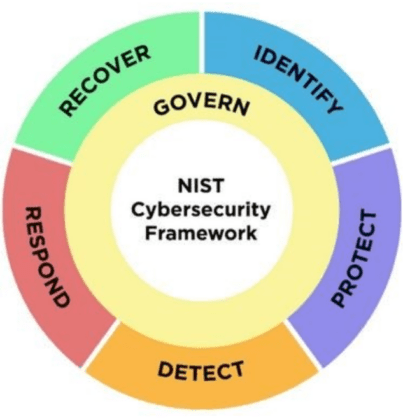
The “Governance” function will focus on the following control categories.
- Organisational Context
- Risk Management Strategy
- Cybersecurity Supply Chain Risk Management
- Roles, Responsibilities, and Authorities
- Policies, Processes, and Procedures
- Oversight
From a local, Irish perspective, CSF is important as the National Cyber Security Centre (NCSC) of Ireland used ?the NIST CSF 1.1 as the base for its NIS Directive Operators of Essential Services cyber security audits. Many organisations, including Ekco, also used adapted versions of CSF 1.1 to deliver cyber security audits in a structured and consistent manner that made sense to organisations, so it has a strong presence in many areas of cyber across the globe.
If you’d like to discuss how to use CSF 2.0 for your company’s cyber security audits, then get in touch.

Question?
Our specialists have the answer
