5 Biggest Microsoft 365 Security Gaps
5 Biggest Microsoft 365 Security Gaps (and how to close them)
Microsoft 365 offers a powerful suite of productivity tools, but its security effectiveness ultimately hinges on your configuration and user behaviour. Here, we explore the top five security gaps lurking in M365 environments, along with actionable steps to close them and strengthen your defences:
1. Weak Passwords and the Absence of MFA
Let’s face it, remembering complex passwords for every application is a challenge. But skimping on password strength is a recipe for disaster. Weak passwords are easily cracked by automated tools, and once an attacker gains access to one account, they can potentially pivot and compromise your entire Microsoft 365 environment.
The good news: Multi-Factor Authentication (MFA) adds a critical second layer of security. Even if a hacker steals a password, they’ll still need a verification code from your phone or another registered device to gain access. Enforce strong password policies and enable MFA for all users – it’s a simple yet highly effective security measure.
2. Unguarded Data Sharing: A Sharing Spree Gone Wrong
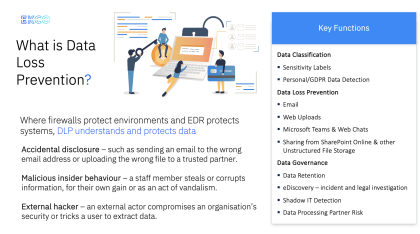
- What is Data Loss Prevention?
Sharing files and collaborating seamlessly are core functionalities of Microsoft 365. However, unrestricted data sharing can expose sensitive information. Imagine accidentally sharing a confidential document with an external party… Almost as bad as texting your friend WhatsApp group a message that was intended for your significant other – compromising, embarrassing & potentially reputation damaging.
Data Loss Prevention (DLP) helps mitigate this risk. DLP policies can be configured to identify sensitive data types (e.g., financial records, customer data) and restrict unauthorised sharing, both internally and externally. Explore DLP features within Microsoft 365 and configure them to suit your organisation’s data security needs, or ask your MSP about it. If only we had DLPs in our personal life…
3. Shadow IT and Unmanaged Devices: The Hidden Threats
Shadow IT refers to unauthorised applications and devices used by employees outside of your IT department’s purview. These “rogue” tools and devices often lack proper security protocols, creating vulnerabilities in your overall security posture.
The answer lies in implementing robust Endpoint Management (EM) solutions. EM allows you to centrally manage and secure all devices accessing Microsoft 365, ensuring they meet essential security standards. This includes enforcing strong authentication, keeping software up to date, and remotely wiping compromised devices.
4. Unmonitored User Activity: A Blind Spot for Security Issues
Suspicious user activity can be a tell-tale sign of a potential security breach. However, without proper monitoring, such activity can go unnoticed for far too long.
Regular monitoring of user activity logs is crucial for early detection of threats. Focus on activities that deviate from normal user behaviour, such as unusual login attempts, access from unauthorised locations, or attempts to download sensitive data. Leverage Microsoft 365’s built-in auditing and logging functionalities, or consider advanced Security Information and Event Management (SIEM) solutions for more comprehensive monitoring capabilities.
5. Limited Security Awareness Training: The Human Firewall We Often Overlook
Even the most robust technical safeguards can be compromised by human error. Employees who lack awareness of cyber threats are more susceptible to phishing scams and social engineering attacks.
Regular security awareness training equips your employees with the knowledge and skills to identify and avoid cyber threats. Trainings should cover topics like phishing email identification, password best practices, and how to report suspicious activity. Remember, a well-informed workforce is a powerful defence against cyberattacks.
By addressing these five common security gaps, you can significantly strengthen your Microsoft 365 security posture. Remember, security is an ongoing process. Stay vigilant, implement best practices, and keep your users informed – together, you can create a secure and productive Microsoft 365 environment for your organisation.

Question?
Our specialists have the answer
