Incident Response & DFIR Services
Leadership and control when it matters most
Rapid Cyber Incident Response & Digital Forensics (DFIR)
In a cyber incident, control is everything.
And when an incident hits, most organisations default to activity. Bridges open. Workstreams spin up. Emails multiply.
What’s often missing is structured incident management.
At Ekco, we lead cyber incidents using a gated, evidence-led methodology refined through years of Digital Forensics and Incident Response work across regulated and enterprise environments.
We don’t just investigate breaches. We impose structure, decision clarity and tempo.

The real risk in a cyber incident
The technical issue is rarely the only problem. What boards and executive teams actually worry about:
- Are we truly contained, or are we guessing?
- Are we preserving evidence for regulatory and insurance scrutiny?
- Who is in charge of decisions?
- Are we aligned to NIS2 reporting clocks?
- Are we about to rebuild systems that are still compromised?
Most incident failures are not technical failures. They are leadership and control failures.
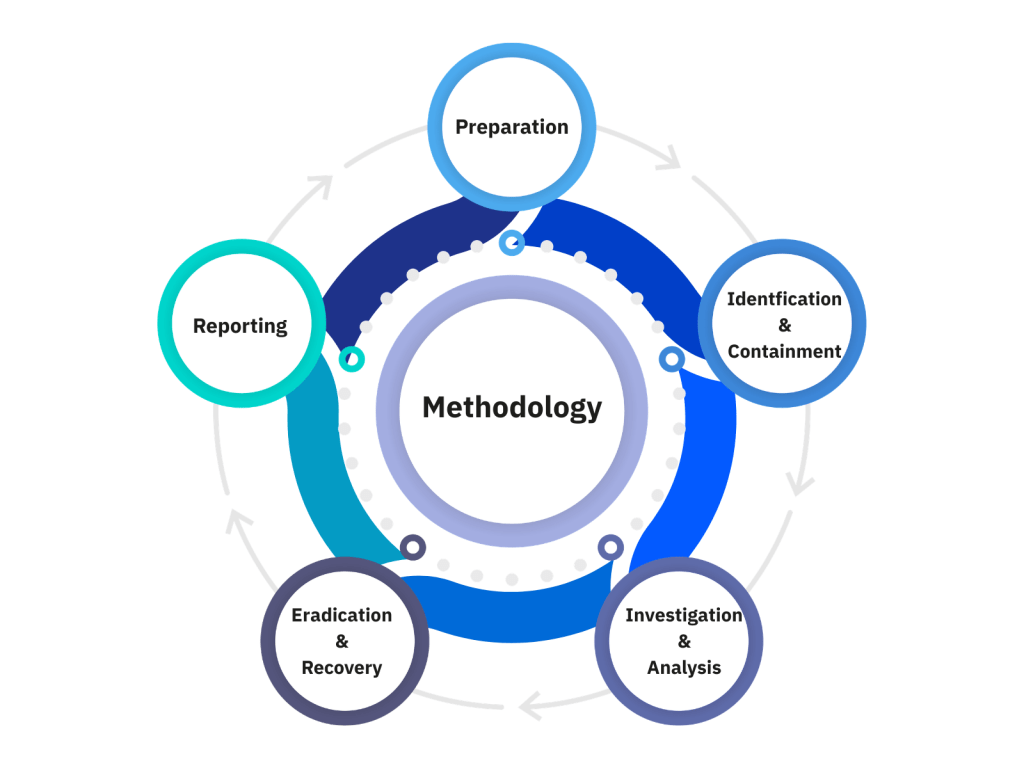
Our Incident Response Methodology
A Gated, Outcome-Driven Lifecycle
We use a structured phase model. We complete the relevant work of a phase, or explicitly log and accept risk before moving forward. This prevents reinfection, regulatory exposure and unnecessary business disruption.
Learn about what attacks we are seeing.
1. Preparation
- Defined roles and ownership
- Workstreams aligned to a single plan
- DFIR tooling validated
- Clear boundaries between IR, crisis comms and executive management
Clarity early saves days later.
2. Identification & Containment
- Validate indicators and confirm what is actually happening
- Establish whether containment has truly been achieved
- Preserve evidence & define timeframe of compromise
- Proactively hunt for additional malicious activity
We stabilise before we accelerate.
3. Investigation & Analysis
- Reconstruct attacker paths
- Validate hypotheses with evidence
- Define blast radius and impact
- Maintain a single control document and decision cadence
We state what is known, what is unknown and what is being tested. No step forward without evidence.
4. Eradication & Recovery
- Controlled rebuild and cleansing
- Secure reconfiguration and hardening
- Coordinated change windows
- Alignment to containment validation, not commercial pressure
We return systems to operation safely, not quickly at any cost.
5. Reporting
- Full incident narrative
- Root cause and attacker techniques
- Regulatory-ready documentation
- Actionable security improvements
Strong reporting protects executive accountability and supports NIS2 obligations.

Why the Gated Approach Matters
In live ransomware and breach investigations we repeatedly see:
- Recovery started before verified containment
- Evidence destroyed during rebuild
- No single incident commander
- Regulatory reporting deadlines missed
- Technical response disconnected from business risk
A structured incident management layer prevents this drift. Workstreams do the work. Incident management controls the outcome.
Consultancy Model or Embedded Support
1. Advisory and augmentative authority
You retain formal incident management ownership. We deliver DFIR, containment, investigation and technical leadership.
2. Embedded incident leadership
Where appropriate, we support or lead the incident management function alongside your executives, aligning technical response with regulatory and business priorities.
In both cases:
- The gated lifecycle remains
- Evidence drives decisions
- A single aligned response plan is maintained
Who we support
CIOs
who need clarity, not noise
CISOs
accountable for regulatory reporting under NIS2
IT Directors
balancing operational restoration with risk
Boards
requiring defensible, documented response actions
When it happens, be ready
Put retained incident response in place before you need it. Fill in your details below to speak to an IR specialist.